WEST MICHIGAN'S MOST RELIABLE
Managed Service Provider
Navigating the constant change of IT can be chaotic and overwhelming, but that's where we come in. As a managed service provider in West Michigan, we organize the chaos and provide structure to improve your confidence that you are addressing the right needs at the right time.
Managed Service Provider in West Michigan
Let us simplify your technology management, ensuring your systems are dependable and efficient so you can focus on running your business.
Manage
“I just need my IT to work when I need it."
Secure
“I need to protect my data and prevent breaches.”
Optimize
“I need IT that adapts quickly.”
We partner with the BESTBRIGHTEST companies in the IT industry
Our partnerships ensure our clients are supported by only the best.





Surprise Out of IT
We’re evolving information technology support. Our managed services customers are not spending time with surprise invoices or requests for unexpected capital expenditures.

Advisory & Support
Looking for an IT company that understands your business? Our team has you covered.

Cisco Webex
Hassle-free video conferencing tools so you can stay connected with your customers.
VoIP Business Phones
Easy to use VoIP phone systems so that you can host webinars and collaborate with your team.

Managed Security
Our powerful managed services bundle covers your end-to-end security needs.
RUN YOUR OPERATIONS WITH MINIMAL DOWNTIME
IT SUPPORT, CONSULTING, & TECHNOLOGY SERVICES
Managed Service Provider in West Michigan
Insights from a West Michigan Managed Service Provider

How to Turn Off Microsoft 365 Copilot Chat
New technology always comes with privacy and safety concerns. It’s great... read more

What is Enterprise Data Protection in Copilot and How Does it Keep You Safe?
If you’ve used Copilot at all since it launched three... read more

Vulnerability Scanning vs. Penetration Testing: What’s the Difference?
As a small business, there is a plethora of cybersecurity... read more

Take the Next Step with Application Whitelisting
Removing local administrator rights used to be the go-to... read more

How to Use the New HT Support App (2026)
Tired of filling out forms and dealing with drop-down menus... read more

Watch What You Click: Attackers Weaponize AI to Spread Malicious Links
Think that website link AI sent you is always safe? Think... read more

Why You Should Always Update Your Browser
You click “Remind me later” on that browser update —... read more

6 Steps to Take After a Data Breach
You get an email from one of your vendors alerting... read more

What is Our Process for Stopping a Spam Bomb Attack?
Spam emails used to be a minor annoyance, but what... read more

Another Microsoft 365 Price Increase Is Coming
Less than a year after raising monthly pricing by... read more

5 Reasons You Should Keep Your Phone Updated
Phone OS updates always seem to come at the worst... read more

Holiday Tech Tip: Shut Down Your Computer Before Your Long Break
Are you the kind of person who shuts down the... read more

Microsoft Lowers Price on Copilot License: What You Need to Know
Have you been curious about Microsoft 365 Copilot but thought... read more

Microsoft 365 Copilot vs. Copilot Pro: Which AI Tool Should You Use?
Editor’s note: This blog was written before the recent introduction... read more

How AI Helps Us Save Hours Every Week and How You Can Too
Have you ever wondered how AI and LLM can streamline... read more

How Hackers Trick You with Fake MFA Resets
Any security-minded organization knows multifactor authentication is a must. <a... read more

The Three Competing Priorities Behind Every IT Decision
Every organization wants technology that’s always available, secure and efficient.... read more

Coinbase Scams: How Do They Work and How Do You Protect Yourself?
Coinbase is one of the world’s largest cryptocurrency exchanges —... read more

What is Global Secure Access?
Are you worried about your remote workers using insecure networks... read more

Microsoft’s Scareware Blocker Protects You Against Full Screen Pop-ups
How many times have you been casually browsing the internet... read more

My Account was Hacked, Now What?
You got an email saying your purchase of Norton Antivirus... read more

Why We Stage Security Incidents and Why It Matters for Your Business
Every managed service provider prepares for the worst and... read more

Why Small Businesses Can’t Skip Detection and Response Anymore
Modern security isn’t just about preventing fires; it’s about knowing... read more

Configure Your Video Conferencing Setup with Cisco’s Workspace Designer
When it comes to configuring a workspace that will host... read more

Why You Should Care About Your Organization’s Security Culture Score
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Traveling for Work? Here are the Best and Worst Ways to Connect.
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Phishing Attacks Can Now Mimic Your Organization’s Login Page in Real Time
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Numbers Don’t Lie: Phishing Training Works
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Ransomware Is Getting Smarter: How AI Is Changing the Threat Landscape
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

BYOD for Smartphones: Balancing Security, Privacy and Cost
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more
Why MDR is the Security Team Your Organization Needs
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Top 3 Cybersecurity Trends We Uncovered from GrrCON 2025
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

The CIA of Data Security: What It Means and Why It Matters
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

What is a Vishing Scam and How Do I Protect Myself?
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Balance in Cybersecurity: Lock the Doors Before Boarding the Windows
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Job Scam Texts are On the Rise: Here are 5 Red Flags to Watch Out For
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Stuck on Windows 10? Here Are Your Options After Support Ends
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

FBI’s Warning: How to Protect Yourself from AI-powered Schemes
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

What is Microsoft 365 Copilot?
Do you struggle to keep up with emails, reports and... read more
Stop Taking Notes in Teams: Let Copilot Do It for You
Paying an extra person to sit in meetings solely for... read more

15 Smart Ways to Use Generative AI
We’ve all been there: Staring at a blank email, forgetting... read more

First Time Using Huntress? Here’s What You Need to Know.
Turning on Huntress for the first time is like flipping... read more

Copilot Can Spot the Excel Mistakes You Miss
Massive Excel spreadsheets can get very messy very quickly, especially... read more

What Coffee Can Teach You About IT Maturity
IT can be complex. Coffee isn’t. When your team scales from... read more

Microsoft Sued for Ending Windows 10: What Does it Mean?
We’re about a month away from Microsoft’s Windows 10 end-of-support... read more

5 Proactive Measures for Small Businesses to Take
Cybercriminals are exploiting software vulnerabilities at unprecedented speeds, potentially costing... read more

Why Passkeys are the Future of Security
Passwords are the weakest link in modern account security, and... read more

Protect Your Clients Against Typosquatting
Misspelling a website address might seem like a harmless mistake,... read more

Here’s What Happens to Your Email Accounts When Merging Companies
Organizational mergers are chaotic, and one thing that tends to... read more

Secure Your Organization’s Applications with Microsoft Entra Private Access
Your employees want the flexibility of working from anywhere, but... read more

Managed Services vs. In-house IT: Which One is Best for Your Organization?
Small and medium-sized businesses (SMBs) rely on technology now more... read more

Use Microsoft Planner to Stay on Top of Your Workplace Tasks
Your boss wants that sales proposal by tomorrow morning, but... read more

How to Use Copilot to Improve and Speed Up Your Email Communications
Does email communication feel like an uphill battle? Between writing, replying... read more

Adobe Will End Support for Acrobat 2020
Adobe recently announced it will end support... read more

VMware Price Hike: What It Means for Your Organization
Migrating business operations to the cloud is growing in popularity,... read more

No, Your Business Doesn’t Get Free Windows 10 Updates
Several news outlets have published articles explaining how to receive... read more

What is Cisco SMARTnet?
Downtime isn’t just a technical hiccup; it’s a nightmare for... read more

7 Questions You Should Ask Before Choosing an IT Provider
Hiring a managed service provider is a high-impact decision. There... read more

Microsoft Isn’t Deleting Your Passwords
Aug. 1, 2025, is an important date for users who... read more

Michigan Pipe Embraces IT Transparency
IT can be messy and complicated. A lot of organizations... read more

Is Your Website Being Maintained for Regular Updates?
A well-maintained website can generate a ton of business for... read more

Why Your Organization Needs Identity Threat Detection and Response
Most security tools watch the doors and windows. Identity threat... read more

What Happens When I Manually Encrypt an Email in Outlook?
Ever wonder if your email truly is private? Even if your... read more

Beware of New Email Attack That Begins with Harmless Spam
Imagine if the spam clogging your inbox wasn’t just a... read more

Secure Your Remote Workers with Microsoft Entra Internet Access
Have you had employees check email or access sensitive company... read more

How to Use Copilot to Summarize Teams Meetings
In a perfect world, every meeting would have a dedicated... read more

3 Signs You’re Being Scammed Over Tariffs
Attackers are using the uncertainty surrounding tariffs to dupe people... read more

Microsoft Ends Business Premium Grants for Nonprofits
Starting next month, Microsoft will discontinue the... read more

5 Common IT Challenges Faced by Small Businesses
Running and maintaining an efficient small business is a lot... read more

Is Your Organization Ready for Copilot? Take This Quick Assessment To Find Out.
You’ve no doubt heard the hype: Microsoft 365 Copilot can... read more

Microsoft Will Raise On-premises Server Prices: What You Need to Know
Microsoft recently announced it is increasing prices... read more

AI Tools and Data Protection: Is It Safe to Use Consumer Versions for Work?
AI tools like ChatGPT and Copilot are great for productivity,... read more

Practical Cybersecurity Advice for Small Businesses
A gazelle living in Africa doesn’t have to be the... read more

Why Risk Assessment is Part of Documenting Critical Applications
We’ve talked before about why identifying your critical applications... read more

4 Essential Tips for Using Your Printer Securely
We put a lot of emphasis on securing networks, servers... read more

Understanding the Levels of IT Preparedness
Unexpected disruptions can cripple your organization. Losing important data can... read more

Why You Need to Upgrade Your Server Operating System
Despite the rise of cloud usage, several organizations still... read more

How to Recycle Old Electronics Responsibly
Do you have old cell phones, laptops or other unused... read more

Meraki vs. Cisco SMB: Which Networking Solution is Right for Your Organization?
Networking hardware is the lifeblood of your organization. A reliable network... read more

Your Granular Admin Relationship: What Does it Mean?
If you’ve been our client for some time, you probably... read more

Dispelling 3 Misconceptions of Microsoft 365 Email Archive
“What’s the difference between my primary email inbox and online... read more

What Parts of Copilot are Free?
Microsoft Copilot has a plethora of features that can help... read more

Why We Recommend Microsoft 365 Business Premium Over Business Standard and Entra ID P1
Choosing the right Microsoft 365 Business plan for your organization... read more

Microsoft Copilot Plans Explainer
Are you interested in trying Microsoft Copilot but not sure... read more

What Does ‘Business-class Email’ Really Mean?
Email has come a long way since the 1990s. And... read more

Trusted Partnership Helps Spring Meadow Flourish
As Spring Meadow Nursery expanded into a 60-acre operation... read more

Why Choose Microsoft 365 Business Basic Over Exchange Online Plan 1?
Finding the right Microsoft 365 Business license for your organization... read more

Microsoft Will End Support for M365 Apps on Windows 10 in 2028 (update)
Editor's note (Update May 12, 2025): Microsoft <a href="https://learn.microsoft.com/en-us/microsoft-365-apps/end-of-support/windows-10-support" target="_blank" ... read more

How to Master Copilot Prompting
Have you ever asked Microsoft Copilot to create a sales... read more

Breaking Down Microsoft 365 Add-ons and Why You Might Purchase Them
We previously discussed all the base Microsoft... read more

What are Copilot Agents and How Can They Help You?
Ever wish you could find your company’s HR policies without... read more
Will Tariffs Make Computers and Other Hardware More Expensive?
If you’ve paid any attention to the news recently, you’ve... read more

What is Microsoft Exchange Online?
Microsoft Exchange Online is for email without the Microsoft Office... read more

What is Microsoft 365 Apps for Business?
Editor’s note: Microsoft is raising prices for all Business licenses... read more

Microsoft Business Licenses and Why You Might Purchase Them
Editor’s note: Microsoft is raising prices for all Business licenses... read more

5 Reasons Proactive IT Management is Critical for Small Businesses
Small and medium-sized businesses (SMBs) face constant challenges to stay... read more

Which Workplace Setup is Best for Your Organization?
As the technology in computers continues to evolve, organizations have... read more

The Dangers of Running Unsupported VMware Software
Imagine this scenario: A cybercriminal finds a weakness in your... read more

Understanding Defensibility: A Moving Target
Let’s be real: no system is 100% secure. Even the best... read more

How MSPs are Adapting to Remote Work
Remote work, once a necessity during the pandemic, has now... read more

Set IT Goals, Prevent Drift and Adapt to Change
One of our clients once said, “My IT is the... read more

What to Expect from a Computer Setup for a New Employee
Hiring a new employee is both exciting and stressful for... read more

What Role Does Teamwork Play in IT Services?
IT has outgrown the days when a single “IT guy”... read more

Microsoft Raising Prices for Microsoft 365 Business Licenses
Microsoft recently announced it will increase monthly pricing by... read more

Our 15-step Computer Setup Process: What to Expect
Computers, unfortunately, don’t last forever. We recommend replacing your computers every... read more

How Copilot AI Transformed Spreadsheet Management for Viking Spas
Maintaining spreadsheets in Microsoft Excel was becoming a burden for... read more

3 Security Measures Your Small Business Should Be Taking
Cybersecurity is hard, complicated and always evolving. It’s quite common for... read more

How Do We Respond to Personal VPN Lockouts?
Lockouts caused by personal VPN usage, while frustrating for employees... read more
Windows Hello and TPM Are the Future of Authentication
Imagine the day when you can log onto your work... read more

Winter Weather Introduces Work from Home Security Issues
As winter storms hit, remote work has made life much... read more

What is a SIM-swapping Scam and How Do I Protect Myself?
As organizations increasingly rely on technology to do business, attackers... read more

How Long Does Microsoft Support Each Version of Windows?
Did you know Microsoft is ending support for Windows 10... read more

Why Buy Equipment Through Hungerford When I Can Get It Cheaper Elsewhere?
Buying equipment through Hungerford or any managed service provider ensures... read more

What Does New Outlook Offer that Classic Outlook Doesn’t?
Microsoft released new Outlook in 2023, featuring a more modern... read more

Why a User-friendly Website Isn’t Optional Anymore
Have you ever visited a website hoping to find more... read more

Change Your Microsoft Sign-in Page to Avoid Man-in-the-middle Attacks
Man-in-the-middle attacks are cyberattacks in which a hacker can steal... read more

Why We Recommend Cable Installation Services
Wireless technology is only going to become more prevalent as... read more

Are You Traveling for Work? Here’s What We Need to Know.
If you’re traveling abroad for work, it’s important you let... read more
Microsoft Ending Support for Mail and Calendar Apps
Editor’s note: We understand most of our clients already use... read more

The Case Against BYOD for Business Security
You should never let employees use their own devices for... read more

Email Examples: What Ends Up in Inbox vs. Junk vs. Quarantine?
If you use Microsoft Outlook as your email client, we’ve... read more

What Should You Do After Falling for a Text Scam?
Have you ever received an innocent-looking text that appears... read more

What Do I Need to Do with Obsolete Equipment?
As technology improves, so will your IT equipment. Hardware will... read more
6 Tips for Decluttering Your Outlook Calendar
Work calendars can get messy. Between regular team meetings, client meetings,... read more

How to Handle Objections with Your Employees When They Defend Keeping Passwords in a File
As people are forced to create more and more online... read more

On-premises Server Makes Sense for Spec Tool
With remote work continuing to rise in popularity, coupled with... read more

What Happens When You Use the Phish Alert Button?
Editor’s note: In recognition of National... read more

Why Keeping a File with Passwords on Your Computer is a Terrible Idea
Editor’s note: In recognition of National... read more

Top 3 Cybersecurity Threats We Uncovered at GrrCon 2024
Editor’s note: In recognition of National... read more

Why Does My Organization Need Cybersecurity Insurance and an MSP?
Editor’s note: In recognition of National... read more

7 Reasons Your Organization Needs Cybersecurity Insurance
Editor’s note: In recognition of National... read more

NIST Releases New Password Rules: What Does It Mean for You?
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

My Dad Lost Thousands in a Romance Scam: How They Work and How to Protect Yourself
Editor’s note: In recognition of National... read more

Early Warning Signs Your Employees Need to Look Out for and Report to IT
Editor’s note: In recognition of National... read more

What is Quishing and How Do You Protect Yourself?
Editor’s note: In recognition of National... read more

Tips for Running an Effective Cybersecurity Awareness Campaign
Editor’s note: In recognition of National... read more

6 Conditional Access Policies You Should Turn on Now
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

What is a Pig Butchering Scam and How Do You Protect Yourself?
Editor’s note: In recognition of National Cybersecurity Awareness Month this... read more

Take Advantage of Tax Benefits by Upgrading to Windows 11 Now
The Windows 10 end date is nearly here. On Oct. 14,... read more

Why Do We Encourage Our Clients to Use Microsoft Edge Over Google Chrome?
Since releasing in 2008, Google steadily captured more and more... read more
How to Access Clipboard History in Windows
If you use the copy and paste commands frequently, you’ve... read more

5 Differences Between Business-grade Computers and Consumer-grade Computers
Not all computers are created equally. There are computers designed to... read more

Are Extended UPS Warranties Worth It?
Recently, we discussed what a UPS is and how... read more

What is a UPS and How Often Should I Replace It?
You may have heard the acronym “UPS” thrown around if... read more

Committed vs. Uncommitted Microsoft 365 Licenses
You’ve probably heard of the different Microsoft 365 plans, which... read more

What to Do if Your Credentials Are Stolen
Editor’s note: If you believe you just actively gave away... read more

What Assets Should I Track for IT Budgeting and Planning?
Failing to plan is planning to fail. The costliest way... read more

4 Reasons Why Your Employees Should Stop Using Apple’s Mail App for Work Email
The iPhone Mail app allows users to access email from... read more

Things to Consider Regarding Hotspots for Your Employees
Hotspots are great for connecting devices to the internet when... read more

IaaS vs. SaaS: Your Guide to Moving to a Serverless Environment
As businesses look to modernize their IT infrastructure, moving from... read more

How Do We Prioritize Submitted Tickets?
Nobody likes dealing with computer issues, especially when it affects... read more

Stories We Help Our Clients Tell: Taking IT More Seriously
Every organization has a unique story that drives its mission... read more

What Do We Audit for in Our Advisory Alignment Process?
Our advisory services proactively ensure your... read more

Did You Get a Scary Email? Here’s What to Do.
Unexpected emails should raise red flags. Especially ones that ask... read more

Password vs. Passphrase: Which One is Better?
Passwords and passphrases are used as authentication measures to access... read more

3 Reasons Your Login Attempt Might Be Denied
"Why can't I access my emails? I'm just trying to... read more

What is the 3-2-1 Backup Rule?
Organizations need to have backups to keep their data safe... read more

How an Incident Response Plan Can Save Your Company
No company is 100% secure from a cyberattack. You’ve no doubt... read more

Why Do I Need Huntress Protection for My Network and Microsoft 365?
You might already have Huntress protecting your network but extending... read more

How to Change Your Email Signature on the Outlook Mobile App
Have you ever received an email from a coworker or... read more
How to Use Daily Focus Plan in Microsoft Outlook to Get Work Done
We’ve previously discussed how using Focus sessions in Windows... read more

Top 10 Cybersecurity Misconfigurations and Why They Matter
Late last year, the National Security Agency (NSA) and the... read more

Never Tell Anyone Your Password, Even IT Staff
As harmless as you might think sharing your password for... read more

Why We Utilize Service Express for Server Warranties
Many organizations have opted to move their operations to... read more

3 Common Security Practices in Cybersecurity Insurance Applications
We’ve noticed a trend working with several organizations: three cybersecurity... read more

What are the Stages of a Cyberattack?
Cyberattacks are scary. Not only can they cost your organization thousands... read more

Why We Recommend Valley City Electronic Recycling
Electronic waste recycling has become increasingly important as we use... read more

What is Microsoft Recall and Why is it Concerning Some Cybersecurity Researchers?
UPDATE (June 14, 2024, 1:42 p.m.): Microsoft... read more
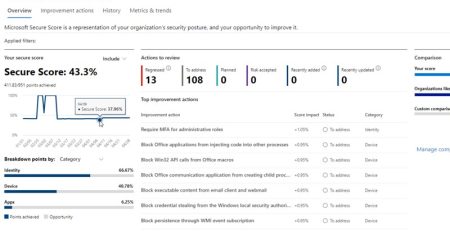
What is Microsoft Secure Score and How Do I Improve It?
Microsoft Secure Score is a tool designed to help organizations... read more

7 Questions to Ask Before Choosing a PDF Editor
Choosing a PDF editor is a lot more nuanced than... read more

Why Would You Tag Someone in an Email?
In real life, nonverbal cues like eye contact make it... read more
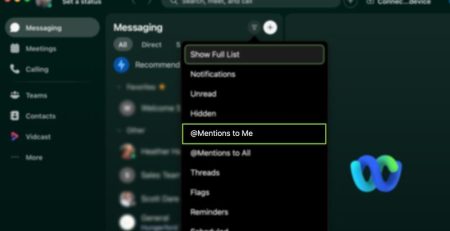
The Art of @ Mentions in Webex Spaces
Why Would You Tag Someone in a Webex Space? In digital... read more
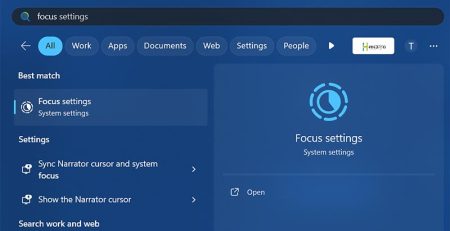
How to Use Focus Sessions in Windows 11 to Get Work Done
Did you know Windows 11 has a built-in productivity tool... read more

Why Did I Get Locked Out for Using a Personal VPN?
Virtual private networks (VPNs) are great for accessing company... read more

Why is Vulnerability Management Important?
Vulnerability management is a continuous and proactive process that keeps... read more

Cell Phone Stipends for MFA in the Workplace
A quick and easy way for organizations to improve their... read more
What are MailTips in Microsoft Outlook?
While composing a message in Microsoft Outlook, you may have... read more

Event Assists Ensure Smooth Meetings for NAHB
When the COVID-19 pandemic hit the United States in March... read more

What are Reporting Requirements After a Data Breach?
We’ve previously discussed the importance of encrypting your data... read more

Debunking the Myths of Registering Your Phone with Your Organization
As a managed service provider for your organization, security is... read more

Windows 11 In-place Upgrade or Clean Install?
Security updates and support for Windows 10 will end Oct.... read more

Planning Your Upgrade from Windows 10 to 11
Next year, Oct. 14, 2025, to be exact, Microsoft will... read more

Microsoft Unbundles Teams and Office: What You Need to Know
Earlier this month, Microsoft announced it will sell its messaging... read more

Why Does Windows 11 Need TPM 2.0?
If your organization is looking to make the jump to... read more

How Do I Identify My Critical Applications?
Critical applications are essential for business continuity. If a business-critical... read more

Is Your Organization an Ideal Fit for Our IT Services?
As we’ve previously outlined, there are several things to... read more

Is it More Secure to Use Cellular Data or Public Wi-Fi?
Thanks to cellular networks, the internet can be accessed from... read more

What Determines Whether an Email Goes to Junk Folder or Quarantine?
If your organization uses Microsoft Defender, you may have received... read more

6 Reasons a Business Password Manager is Better Than a Personal One
Password managers are a great tool for your employees to... read more

The 5 Pillars of an Effective Cybersecurity Solution
Cyberattacks continue to grow — not just in frequency but... read more

Why We Recommend Microsoft 365 Business Premium to Our Clients
Editor's note: Beginning April 1, 2025, Microsoft raised prices for... read more

How to Modify Outlook Calendar Sharing Permissions
Microsoft Outlook allows people in your... read more
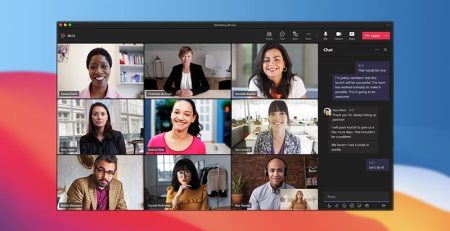
What You Need to Know About the New Microsoft Teams
In October 2023, Microsoft announced the general... read more

What is Our Process for Stopping a Phishing Attack?
If not properly detected and addressed, phishing attacks can cost... read more

Migration to Cloud Offers Convenience for Paws With A Cause
Cloud services continue to grow in popularity, and while there... read more

How to Use Microsoft Loop to Create To-do Lists
Between email; instant messaging services like <a class="hide-link" href="https://www.webex.com/" target="_blank" ... read more

What is the Value of Technology Alignment?
Companies are relying on IT more than ever. While IT wasn’t... read more

Should I Upgrade, Repair or Replace My Computer?
You’ve likely run into this situation once or twice before.... read more
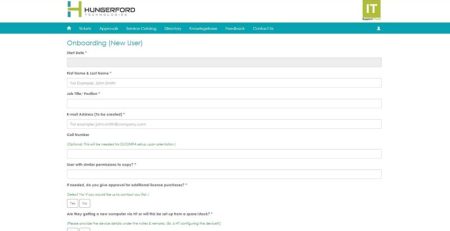
How to Submit Employee Onboarding Requests Through the HT Support App
Editor's note: Employee onboarding requests are now done through the... read more

Is Your Organization Ready for Windows 11?
Microsoft will be ending support for Windows 10 in 2025,... read more

VPN vs Cloud Storage: Which is Best?
COVID-19 forced a lot of the <a class="hide-link" href="https://www.forbes.com/advisor/business/remote-work-statistics/" target="_blank" ... read more

How to Send an Encrypted Email in Microsoft Outlook
If you’ve ever had to send highly sensitive information digitally,... read more

How is an Offboarded Employee’s Email Handled?
After an employee is terminated or leaves voluntarily, organizations must... read more
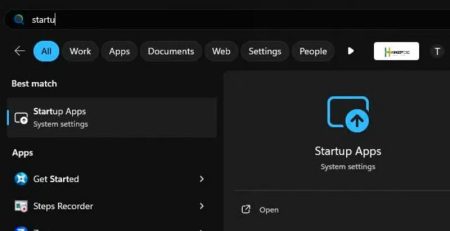
How to Enable and Disable Startup Applications
If you notice your relatively new computer is starting to... read more

What is Microsoft Loop?
Collaboration between team members and departments can be a headache,... read more

Beware of Emails That Ask for Login Credentials
IT security tools are complex and difficult to bypass, so... read more

Who is Not a Good Fit for Our Phone Systems?
Finding the right business phone system can be overwhelming for... read more

Who is a Good Fit for Our Phone Systems?
Finding a business phone system can be a hard and... read more

Employees Using a Personal Computer to Access Work Data is a Bad Idea
Remote work probably isn’t going away anytime soon. And because... read more

What are Phishing Attacks Attempting to Accomplish?
Phishing attacks have skyrocketed just in the past year, and... read more

Why is 3 to 5 Years the Recommended Replacement Timeframe for Computers?
Computers are essential in today’s workforce; unfortunately, they have a... read more

Are You on the Naughty List of Bad Password Usage?
The holiday season is upon us, and with it comes... read more
How to Send Meeting Availability in Outlook
Have you ever had a back-and-forth email conversation trying to... read more

How to Avoid Shipping and Phishing Scams During the Holidays
While Black Friday, the busiest shopping day of the year,... read more

Why You Should Upgrade Your Windows Operating System
Software upgrades have become an essential — albeit annoying —... read more

5 Signs You Might Need New Computers
Everyone loves the feeling of booting up their brand-new computer... read more

Get Up and Running With the Webex Calling App in Just 11 Minutes
The Webex Calling app is a cloud-based phone service that... read more

What is Single Sign-on?
Single sign-on (SSO) is an authentication method that allows users... read more

Why Do MSPs Use Ticketing Systems?
If you’ve ever had to contact your managed service provider... read more

What are the Differences Between Windows 10 and Windows 11?
When Microsoft released Windows 11 about two years ago, it... read more

Wright Plastic Products Values ‘Knowledgeable’ HT Staff to Tackle Co-managed IT
John Christiansen has a lot on his plate. The IT operations... read more

5 Factors That Determine Cost of a New Phone System
There’s a lot that goes into purchasing a new... read more

What is a VPN and Why Might You Need One?
If you’ve had to access company files or data when... read more

How to Stay Secure: A Roundup of 7 Educational Cybersecurity Blog Posts
Editor’s note: October is National Cybersecurity... read more

Multifactor Authentication Prompt Bombing: What Is It and How Do You Protect Yourself?
Editor’s note: October is National Cybersecurity... read more

Avoid These 6 Cybersecurity Myths and Misconceptions
Editor’s note: October is National Cybersecurity... read more

Microsoft Ends Support for Windows Server 2012 and 2012 R2: What Does That Mean for Your Business?
Editor’s note: October is National Cybersecurity... read more

3 Cybersecurity Measures SMBs Should Implement Now
Editor’s note: October is National Cybersecurity... read more

Follow These 3 Rules to Avoid Online and Phone Scams
Editor’s note: October is National Cybersecurity... read more

How Does Security and Privacy Work with Microsoft 365 Copilot?
Editor’s note: October is National Cybersecurity... read more

What is the Process for Purchasing a New Phone System?
Just like old computers can prohibit you and your employees... read more

Is a Managed Service Provider Right for Your Business?
Owners of small- and medium-sized businesses have a lot on... read more

How do Data Breaches Happen?
You’ve no doubt seen news coverage of big-scale data breaches.... read more

Why is a Business Password Manager Different from a Personal Password Manager?
It’s a must for businesses to train their employees on... read more

What is the Average Lifespan of a Computer?
Aging computers not only are frustrating to use, but they... read more

Why Do IT People Ask Me to Clear My Cache?
If you’ve ever had problems logging on to a website... read more

Is My Data Safer in the Cloud?
Saving documents, photos, videos and other files on a hard... read more

HT Helps The Gabriel Group Employees Improve Organizational Security
In May 2023, The Gabriel Group switched... read more

How to Review Quarantined Emails in Microsoft Outlook
To protect you from spam or suspicious-looking emails, <a class="hide-link" ... read more

As Phishing Attacks Surge, It’s Important to Take Phishing Training Seriously
Technology is constantly improving to secure your sensitive data, making... read more

What Are Bing Chat Enterprise, Microsoft 365 Copilot and How Can They Help Your Business?
Ever since ChatGPT was released last year, businesses have... read more

FTC Safeguards Rule Provisions: We Can Help
In November 2022, the Federal Trade Commission (FTC) extended the... read more

What is Two-factor Authentication?
Two-factor authentication (2FA), also referred to as multifactor authentication, is... read more
3 Times You Should Not Accept Cookies
Cookie popups are everywhere. There’s no doubt you’ve experienced one... read more

What Are Cookies and Cache on My Computer?
If you’ve spent any amount of time using the internet,... read more

Why Does Turning Your Computer Off and On Again Work?
Have you ever dealt with slow internet, only to fix... read more
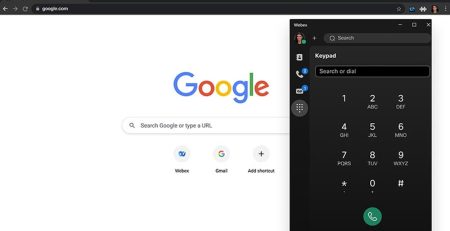
How to Use Webex Calling for Chrome
Webex Calling for Chrome allows you to place and receive... read more

Why You Need to Stop Using the Same Password on Multiple Accounts
It seems like every basic online activity you need to... read more

What to Expect When Getting a New Computer
There’s nothing like that feeling of getting a new computer.... read more

How Do You Prolong the Lifespan of Your Computer?
The business world relies on computers today more than ever.... read more

What is the My Apps Section in the HT Support App?
In addition to submitting a ticket and... read more

How and When to Start a Chat with a Support Technician
Sometimes you have an issue that doesn't merit a phone... read more

How and When to Submit a Ticket Using the HT Support App
Editor's note: We upgraded our support app in 2026. <a... read more

4 Reasons Why You Should Enable BitLocker on Your Organization’s Devices
BitLocker is an important cybersecurity tool that encrypts the... read more

Why it’s a Bad Idea for Businesses to Allow Local Administrator Access
One of the best things companies can do to keep... read more
7 Common Questions People Ask Before Purchasing a New Phone System
Webex Calling is a cloud-based phone system that uses <a... read more

What is Microsoft Windows Patch Management?
Software updates, or patches, have become an essential — albeit... read more

Keep Email Organized with Outlook’s Focused Inbox
Do you sit down at your desk every Monday morning... read more

What is the Dark Web and What is Dark Web Monitoring?
Beyond the traditional websites that are indexed by search engines... read more

Why You Should Use a Password Manager Instead of Your Web Browser to Save Passwords
As we increasingly rely on technology to accomplish everyday tasks,... read more

How Much Does It Cost to Hire a Managed Service Provider?
Managed service providers offer several IT-related services —... read more

Why You Should Hire a Managed Service Provider
Managed service providers (MSP) offer outsourced IT services to small-... read more

How do I Know if My Password is Strong?
As we increasingly rely on technology to accomplish everyday tasks,... read more

What is a Managed Service Provider?
When most people think of IT services, they think... read more

How Can Managed Service Providers Use AI Chatbot Technology?
Chatbots are becoming increasingly popular among all companies regardless of... read more

What is the Difference Between Spam and Phishing?
Spam and phishing have been around since the rise of... read more
Things You Should Know About the LastPass Breach
In August 2022, LastPass experienced a data breach. In light... read more

Why It’s OK to Upgrade to Windows 11 Now
Microsoft released Windows 11 in October 2021, and with it... read more

Should You Move to a VoIP Phone System?
Dropped calls shouldn't be an issue anymore in 2022, but... read more

Can Your Business Support a Remote Workforce?
Remote work has been revolutionized and really pushed forward by... read more

How VoIP Can Improve Customer Service
Modern consumers are pickier and more difficult to satisfy than... read more

Mandatory 10 Digit Dialing for National Suicide Prevention
Starting July 16, 2022, the Federal Communications Commission (FCC) is... read more
Tips for a Smooth Virtual Conference Call
With the pandemic making remote work mandatory for a lot... read more

Top VoIP Phone System Features
Communications for both businesses and individuals have come a long... read more

Does a VoIP Phone System Make Sense for Your Business?
VoIP (Voice over Internet Protocol) is an internet-based phone service.... read more
How to Screen Share in Webex
If you’ve ever been in a virtual meeting, you’ve probably... read more

How to Optimize Your Internet Connection for Webex Meetings
When you’re working from home, the last thing you want... read more

HT Joins the Technology Council of West Michigan
Our President Matt Clarin was recently invited to join the... read more

How to Troubleshoot Bad Video in Webex Meetings
Video calls are essential to staying connected to coworkers and... read more

How to Troubleshoot Bad Audio in Webex Meetings
It’s impossible to have a productive Webex meeting if your... read more

How to Troubleshoot Joining Webex Meetings
Most of the time, joining a Webex meeting is as... read more

How to Use Polls in Webex Meetings
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

The New Webex Meetings Breakout Sessions
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more
The New Webex Assistant for Webex Meetings
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

How to Test Your Webex Meeting Connection
You don’t want to find out in the middle of... read more

The New Look and Feel of Webex
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

How to Optimize Your Meeting Room Technology Using Webex
Finding the right hardware for your meeting space helps increase... read more

Choosing the Best Video Conferencing Equipment
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

Joining a Meeting or Conference Call by Phone
Let’s set the scene: you’re halfway through your daily video... read more

Get the Most out of Webex Teams
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

What To Do When You Can’t Connect To a Webex Meeting
Remote work has its perks. But fighting with your WiFi... read more

Choosing the Right Webex Plan
Every Wednesday, Hungerford Technologies presents an episode covering a hot... read more

How to Choose Remote Meeting Technology
Not all virtual meeting rooms were created equal. Finding the... read more
Getting started With Webex Teams
How To Use Webex Teams Download the desktop and <a href="https://www.consumer.ftc.gov/articles/0018-understanding-mobile-apps" ... read more

Webex Best Practices When Working Remotely
Webex is a collaboration tool that allows you to schedule,... read more

Considerations for Closing the Office and Working Remotely
Due to the uptick in recent question about enabling a... read more

Is Your Tech Support Rep Acting as Your IT Security Consultant?
Tech support exists on a spectrum. On one side of... read more

The Difference Between Help Desk & Full-Service IT Support
For businesses that outsource some or all of their IT,... read more
5 Ways to Improve Your Line Charts in Excel 2016
Many business owners and employees use Microsoft Excel 2016 to... read more

Why PowerPoint’s Grouping Feature Doesn’t Always Work
Microsoft PowerPoint’s grouping feature can be quite useful when creating... read more

Convenient Calling Features That Can Boost Productivity
Employees tend to have many responsibilities, especially in small businesses.... read more

How to Transform a Table into a Chart in Microsoft Word
Microsoft Excel is well-known for its ability to turn tables... read more

Help! I Spilled Coffee on My Keyboard
It is hard to resist the temptation of sipping a... read more

How to Extract Text from Images Using OneNote
Have you ever encountered information in a picture that you... read more
Changing the Setting for the Sleep Timer in Windows 8 & Windows 8.1
The sleep mode is designed to save energy and battery... read more
10 Keyboard Shortcuts to Use When Presenting PowerPoint Slideshows
*This post contains Amazon Affiliate links In business meetings, you can... read more

How to Use iOS 12’s Enhanced ‘Do Not Disturb’ Feature
Sometimes it is important to keep calls and other notifications... read more

Business Benefits of Video Conferencing Tools
Video conferencing is no longer a premium option reserved for... read more

What’s the Best Way to Engage Your Virtual Team?
The benefits of remote workplaces are clear to just about... read more