What is Two-factor Authentication?
Two-factor authentication (2FA), also referred to as multifactor authentication, is an extra security step that requires users to provide two or more different ways — or factors — to verify themselves.
Typically, the two factors are something you know (a password) and something you own (a smartphone). A second factor also could be something you are (a fingerprint or face ID) or somewhere you are (connecting from inside your business).
Why is Two-factor Authentication Important?
It’s easier to steal one thing than two. Requiring a second factor adds a second level of security and helps prevent unauthorized access to sensitive data and systems.
- Without 2FA enabled, if an attacker has your password, then they have access to your account.
- With 2FA enabled, they will be unable to access your account without the second factor, like having your smartphone.
It’s relatively easy for passwords to be stolen. They can be stolen directly from you by tricking you into giving attackers your passwords through email phishing or other social engineering attacks, but they also can be stolen without you doing anything wrong.
You aren’t the only one who knows your passwords; the service you are logging into also knows it. If that service gets breached, then every username and password they know could get posted on the dark web, and then, through no fault of your own, your password is stolen.
“It’s always recommended to use 2FA where it is offered, but especially important for any account that has financial or personal information.”
It’s always recommended to use 2FA where it is offered, but especially important for any account that has financial or personal information. Bank accounts, payment apps (PayPal, Venmo, Zelle, etc.) and health system accounts should always be protected with 2FA.
In his blog post, Your Pa$$word doesn’t matter, Microsoft Vice President of Identity Security Alex Weinert states, “Your password doesn’t matter, but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
Why Do Some Organizations Not Enforce Two-factor Authentication?
Despite how critically important 2FA is, some organizations don’t enforce it on their employees.
One of the reasons is that it requires employees to have their phones with them during working hours. If they travel to work and forget their phone, they can’t log in to any business-critical software, which means they must drive back.
It’s embarrassing for the employee and wastes time, but it’s safer for the organization.
Additionally, the initial setup to get every employee configured is disruptive. However, that’s where we as a managed service provider can help streamline the process and lessen the disruption so your employees can remain productive.
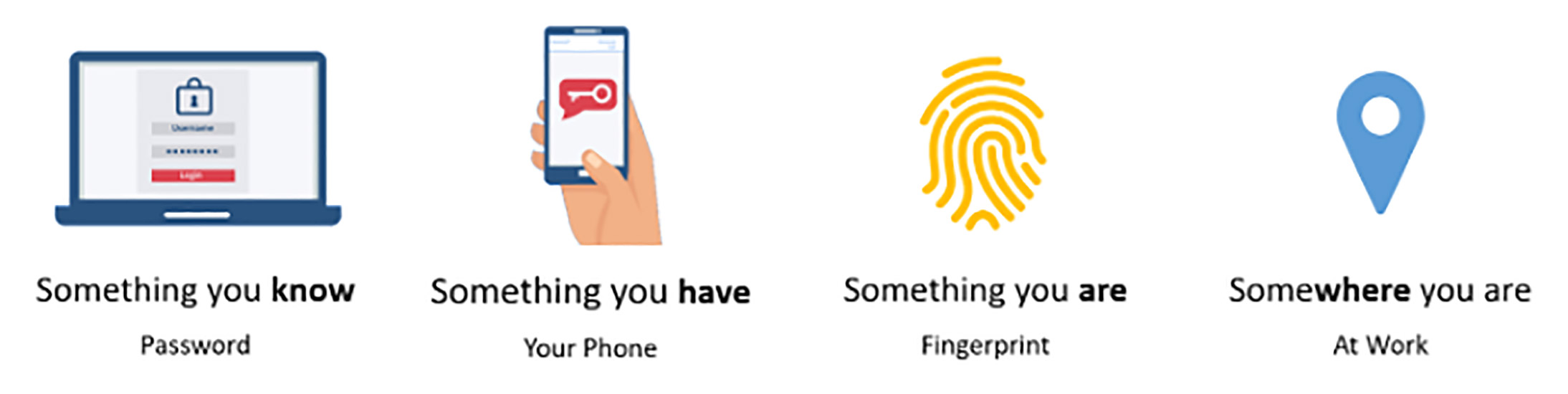
What are Some Examples of Two-factor Authentication?
As stated earlier, the first factor when trying to log in to your account is something you know, such as a password or security code. When you have 2FA enabled, you will have to provide a second factor to access the account.
A second factor could be:
- Something you have
- A one-time code you can access using an authenticator app on your smartphone: Authenticator apps can store one-time codes for your accounts. The codes are constantly regenerated so a code cannot be used multiple times.
- A push notification sent to your smartphone: A notification will pop up on your screen, and you will have to allow or deny the request.
- A one-time code sent to your mobile phone via text message: The message generally will state the account you are trying to access and notify you the code will expire after several minutes.
- A physical device that acts like an electronic key to gain access: Generally the size of a flash drive, these devices must be plugged into your computer or they have small LCD screens that generate a one-time code.
- Something you are
- A biometric, such as a fingerprint or face ID: Most phones have fingerprint ID or face ID to confirm you are who you say you are.
- Somewhere you are
- Geolocation security checks make sure a user is located where they say they are using an IP address. It’s also common to use location to reduce the number of 2FA prompts for employees physically in the office as opposed to those connecting from their homes.
Many second factors involve a code or notification sent to your smartphone. As most people have smartphones and take them wherever they go, this is a good way to secure your accounts.
To balance security, costs and ease of use, most of our clients use a password in combination with an authenticator app.
Even if your smartphone is compromised, an attacker would need to know your phone’s PIN, pattern or use your biometrics to unlock your phone, essentially adding a third factor of authentication.
Of course, entering a second code to access an account can be cumbersome and annoying, but the pros of adding an extra layer of security far outweigh the cons of taking an extra step to log in to your accounts.
West Michigan Managed Service Provider
Need help finding the right 2FA solution to protect your network and data? Contact Hungerford Technologies to see how we can help keep your business running smoothly while increasing productivity, security and profitability.











