Beware of Emails That Ask for Login Credentials
IT security tools are complex and difficult to bypass, so the easiest way for attackers to breach a network is to trick employees into handing them the keys.
Phishing attacks surged in the first half of 2023, according to a report by Acronis, which is why we previously discussed the importance of taking phishing training seriously.
An emerging trend we are seeing is a specific kind of phishing attack, the Microsoft 365 redirect phishing scam. This scam tricks you into entering your login credentials on a fake website that mimics the real Microsoft website.
The tactics used to do this vary, but the general goal is to make you think you need to log into your Microsoft account to view a shared file, enable a tool or resolve an issue.
Here are a few examples of phishing emails you might see.
- An email that asks you to open the attached document
- An email that asks you to update your password
- An email that says your sent email was not delivered and you must sign in to resolve
- An email that says a new security tool was activated for your Microsoft account and you must sign in to enable
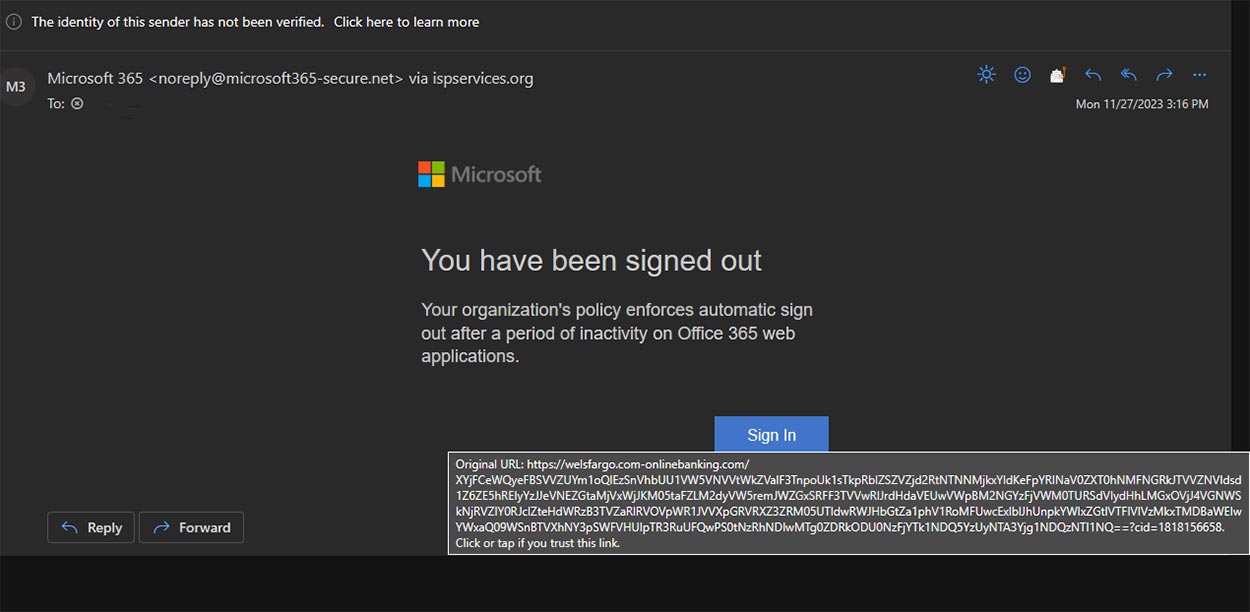
- An email that says you have been signed out of your Microsoft account
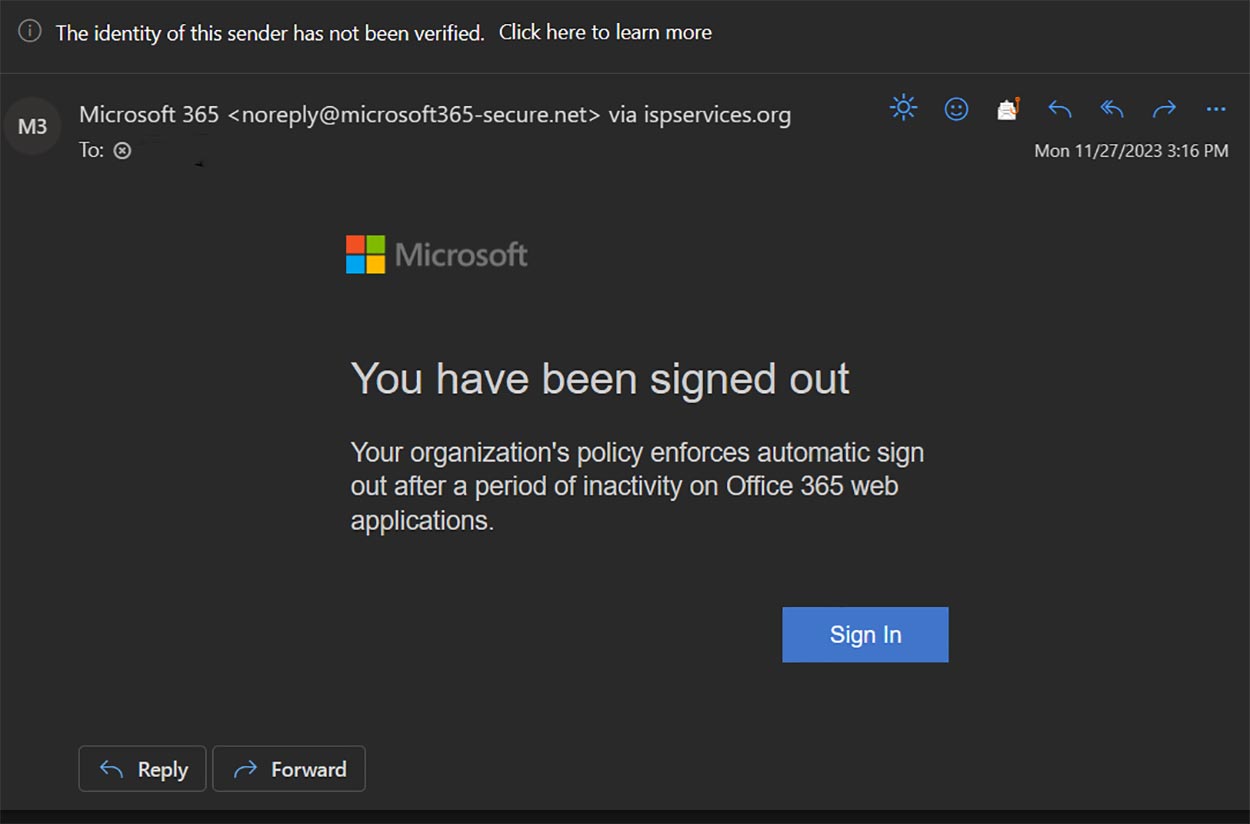
As you can see in the screenshot above, the email appears to be from Microsoft; it’s formatted to look like an official message from Microsoft.
Organizations very rarely send emails like this asking you to update information or log in to reinstate your account. Instead, when you log in to the actual account, you may get a popup or notification to ensure information is still up to date. In this case, you know it’s legitimate because you’ve logged in to the correct website.
The goal of the Microsoft phishing attacks is to get you to enter your login credentials so the attacker can log in to your account as you. Even if you have multifactor authentication enabled, these fake pages allow them to steal that so they can have the second factor needed to access your account.
So how do you protect yourself and your organization from these specific types of phishing attacks?
“If you’re still unsure whether an email is legitimate, verify with the sender through a different medium. You can either start a new email with the proper contact or try calling the contact directly to verify if the email they sent came from them.”
Follow These 3 Steps to Protect Yourself
- Always stop, look and think before you click
- Check for red flags that indicate a phishing attack is happening
- Verify suspicious emails with the sender through a different medium
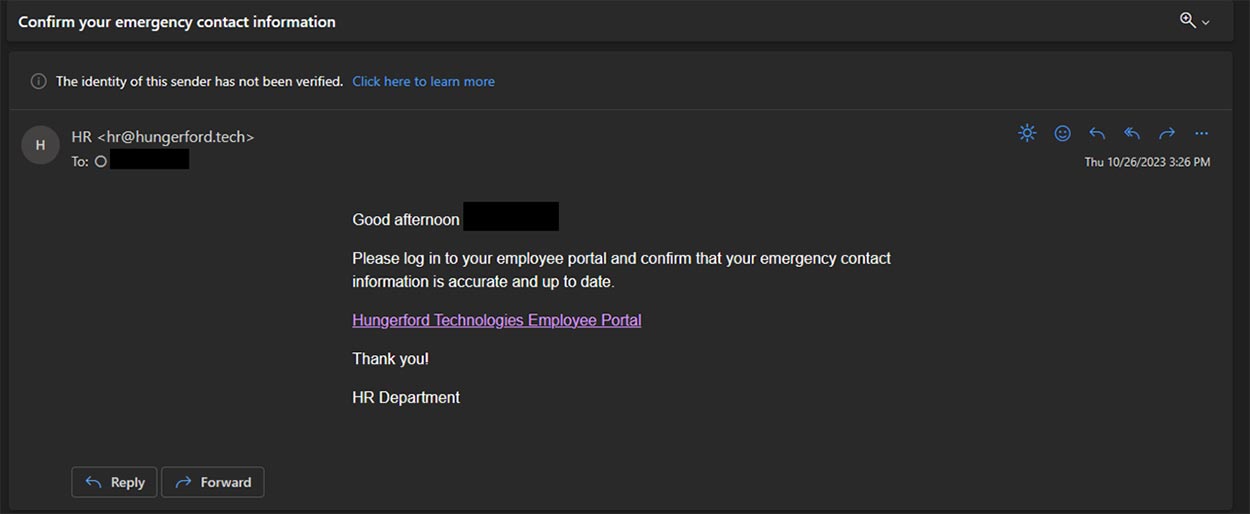
The screenshot below is an example of how a phishing attack will attempt to deceive you into logging in to your account to update emergency contact information. While this example is not from Microsoft, the tactics still are the same.
What are the Red Flags?
As we stated earlier, if you get an email like this that asks you to re-login, update information or reinstate your account, that should be a cause for concern.
If you think the email is legitimate, go to the website yourself rather than clicking the link from the email.
Some main red flags to watch out for include:
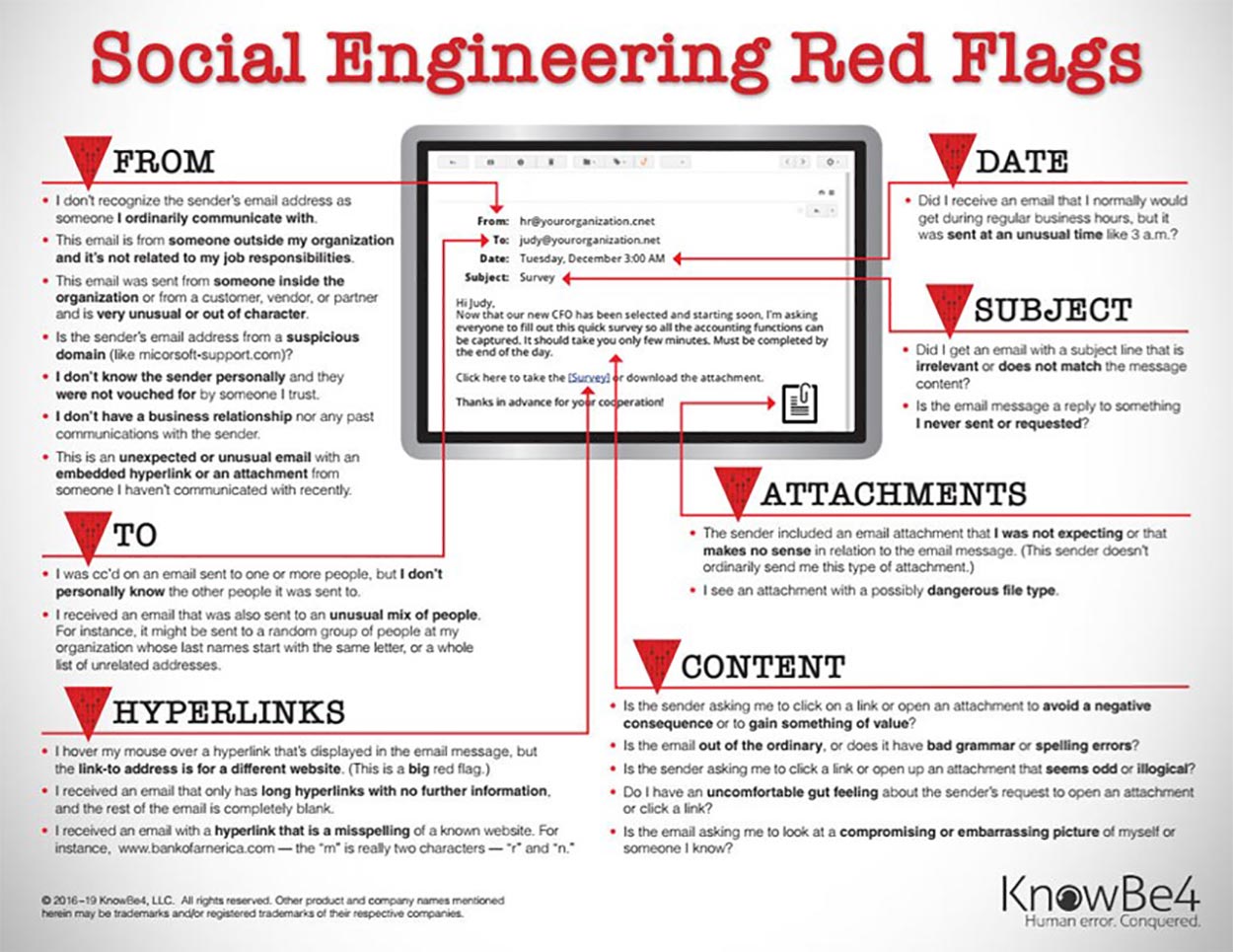
Fake email: In the examples, noreply@microsoft365-secure.net and hr@hungerford.tech are fake email addresses. Microsoft Outlook even flagged both as possibly illegitimate with a note at the top that says, “The identity of this sender has not been verified.” That doesn’t mean anytime you see that message that it is a phishing attack, but it’s worth investigating more if you do see this message.
Fake link: If you hover your mouse pointer over the link, Outlook will show you the address the link will take you to. You can see in the example below the link is way too long and does not direct you to the proper HR website.
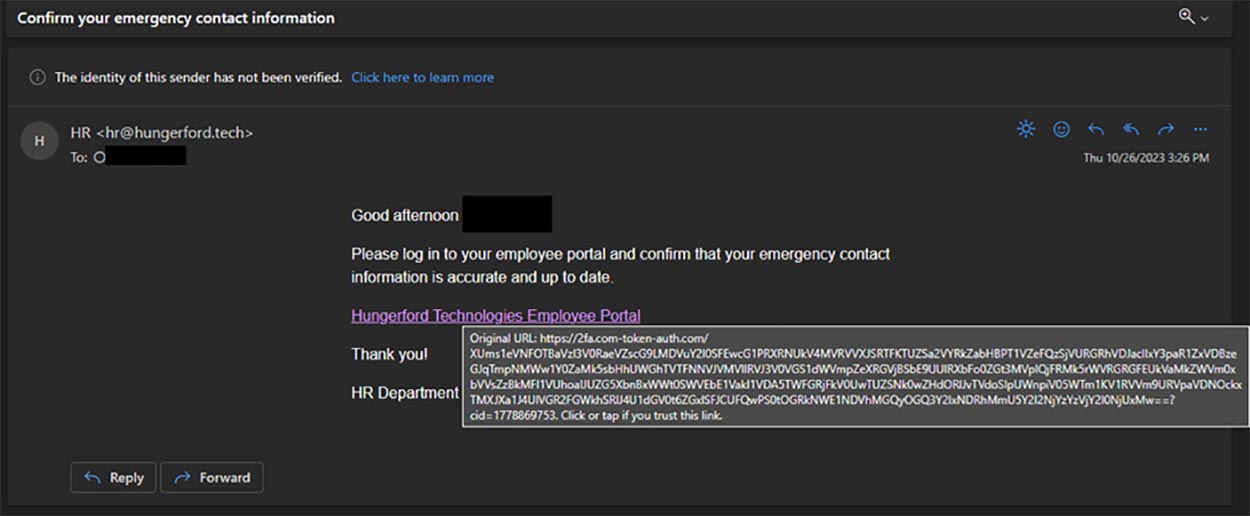
Generic signature: Because these attacks often are sent in bulk, the attacker usually ends the email with a generic signature. In the HR case, it ends with “HR Department.”
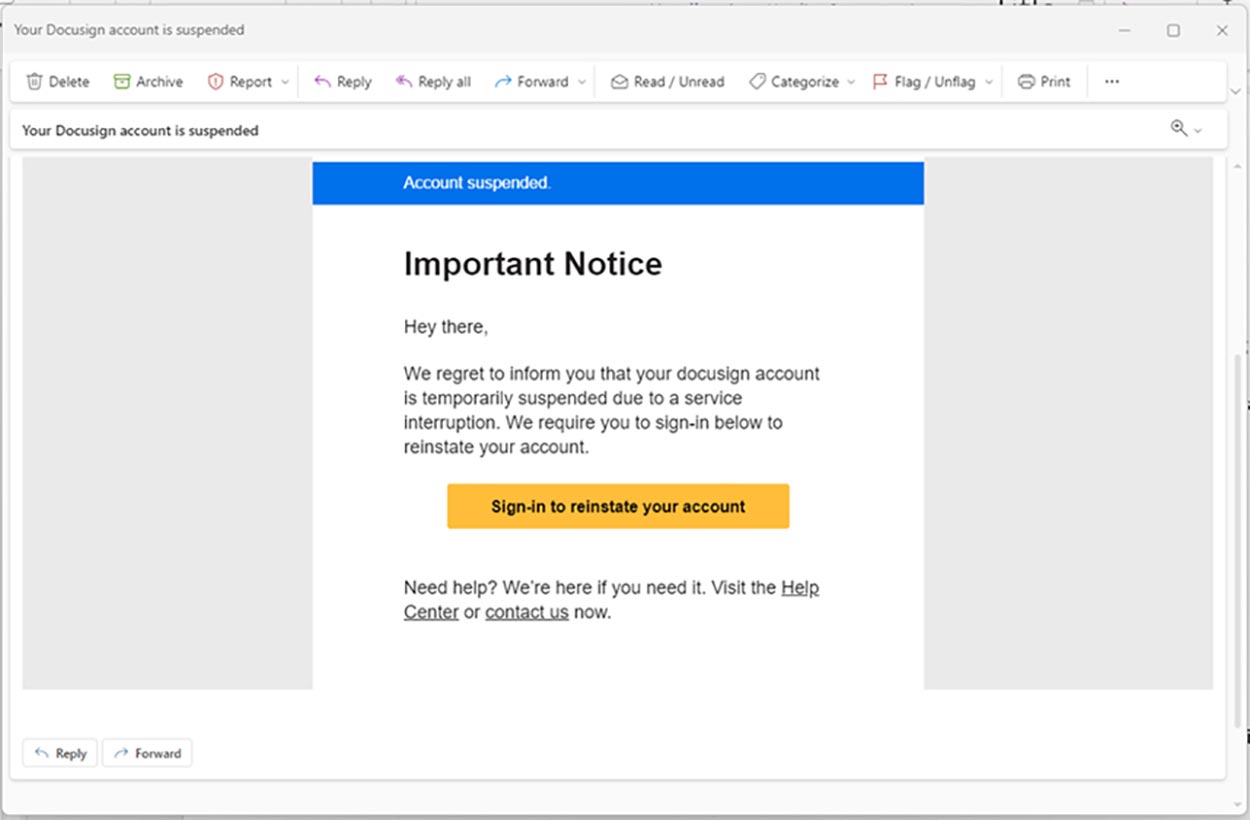
Misspelling or grammar errors: Attackers don’t tend to be English majors and often will make spelling or grammatical errors. In the example below, the attacker doesn’t properly format the word “DocuSign,” a huge red flag as the real DocuSign organization wouldn’t format the name of its own company wrong in an email.
Password manager doesn’t autofill: With the autofill function turned on, password managers won’t autofill your username and passwords on fake websites. If you visit a website from an email link and notice your credential information isn’t automatically filled in, that should make you pause.
If you’re still unsure whether an email is legitimate, verify with the sender through a different medium. You can either start a new email with the proper contact or try calling the contact directly to verify if the email they sent came from them.
In the examples above, that would include contacting a specific person from the HR department or customer support at Microsoft or DocuSign. But if that sounds like too much work, you can always delete the email and ignore it, which is better than forwarding the email to your employees or IT department to ask if it is legitimate.
The key is to treat any email as potentially harmful. It’s easy to fall into a lull and click a link without thinking. Be vigilant, and you’ll be doing your part to protect yourself and your organization.
Learn More About Phishing Training
Looking to protect your company from cybersecurity threats? Contact us here to learn how we can help secure your sensitive data.