The CIA of Data Security: What It Means and Why It Matters
Editor’s note: In recognition of National Cybersecurity Awareness Month this October, we are publishing a series of blog posts dedicated to educating and informing you about cybersecurity practices. This is the sixth in a series of posts. Below, you can find a list of links to the rest of the series:
- FBI’s Warning: How to Protect Yourself from AI-powered Schemes
- Stuck on Windows 10? Here Are Your Options After Support Ends
- Job Scam Texts are On the Rise: Here are 5 Red Flags to Watch Out For
- Balance in Cybersecurity: Lock the Doors Before Boarding the Windows
- What is a Vishing Scam and How Do I Protect Myself?
- Top 3 Cybersecurity Trends We Uncovered from GrrCON 2025
- Why MDR is the Security Team Your Organization Needs
- BYOD for Smartphones: Balancing Security, Privacy and Cost
- Ransomware Is Getting Smarter: How AI Is Changing the Threat Landscape
- Numbers Don’t Lie: Phishing Training Works
- Phishing Attacks Can Now Mimic Your Organization’s Login Page in Real Time
- Traveling for Work? Here are the Best and Worst Ways to Connect.
- Why You Should Care About Your Organization’s Security Culture Score
Every organization worries about its data, but not always for the same reasons. Some fear leaks, some fear manipulation and others fear downtime.
Together, these concerns form the foundation of data security: the CIA triad.
- C: Confidentiality
- I: Integrity
- A: Availability
Each principle addresses a different kind of threat. We’ll define each principle and discuss a real-world scenario so you can better understand what your organization values the most.
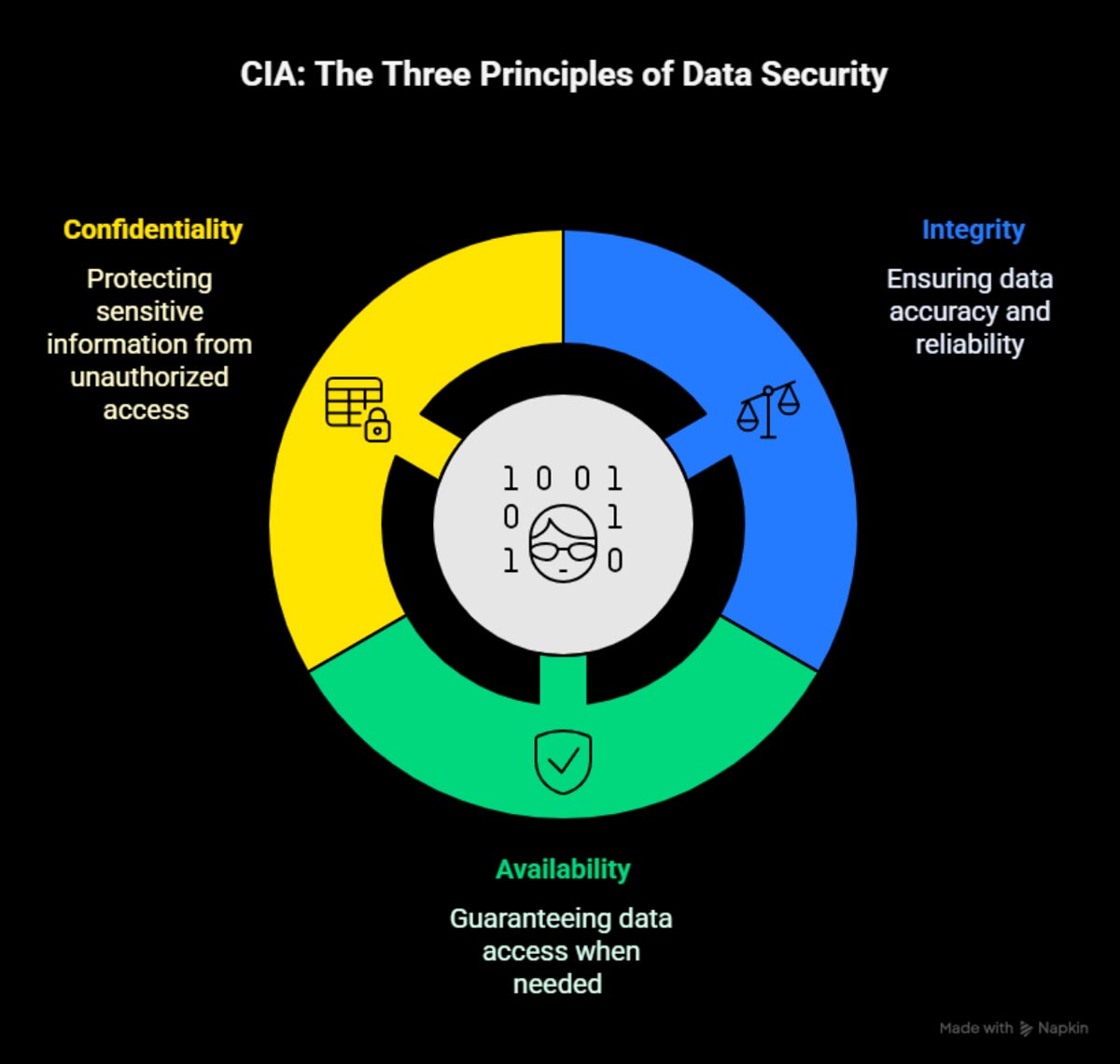
Confidentiality: “I don’t want anyone to see my data”
Confidentiality is all about keeping your data private from unauthorized users. Not only does that mean keeping your data secure from those outside of your organization, but it also means ensuring only those with proper authorization inside your organization have access to it.
Real-world Scenario: A local accounting firm stores client tax returns.
Risk: If the firm’s systems aren’t secure, an unauthorized person could access sensitive data (e.g., Social Security numbers, financial information, etc.).
Solution: The firm uses encrypted file storage and requires multifactor authentication to ensure only authorized employees can access client records.
Expert Insight: For professional services firms — law, accounting, financial advisors — confidentiality is the top concern. Their entire reputation depends on keeping client data secure. A single breach can destroy trust, trigger compliance issues and, ultimately, threaten the business’s survival. Nonprofits face a similar challenge when protecting donor information. If sensitive donor details are exposed, the organization risks both reputational damage and loss of future support.
Integrity: “I don’t want anyone to manipulate my data”
Integrity ensures your data is accurate, trustworthy and free from tampering. This includes public information found on your website or private information stored on servers or in the cloud.
Real-world Scenario: A local medical clinic maintains electronic health records.
Risk: A cyberattack alters patient allergy information or prescription details. Even a small change could put patient safety at risk and expose the clinic to liability.
Confidentiality is all about keeping your data private from unauthorized users. Not only does that mean keeping your data secure from those outside of your organization, but it also means ensuring only those with proper authorization inside your organization have access to it.
Solution: The clinic protects data integrity with audit logs that track changes, access controls that limit who can update records and regular validation processes to confirm information is accurate.
Expert Insight: For most SMBs, integrity comes third. They’re usually focused on keeping data private (confidentiality) and systems running (availability) before worrying about tampering. Implementing advanced integrity controls can feel overwhelming when day-to-day demands are already stretching IT resources. That said, even simple measures like keeping audit logs and limiting who can make changes to critical data can go a long way toward preventing costly mistakes or compliance headaches.
Availability: “I don’t want business operations to stop”
Availability is about making sure your systems, networks and applications stay up and running when you need them. Downtime can be a minor annoyance or a business-critical disruption.
Real-world Scenario: A local florist relies on an online store to sell flowers for Valentine’s Day.
Risk: The florist’s website goes down during peak holiday traffic, resulting in lost revenue.
Solution: It uses a hosting service with high uptime guarantees, backup servers and DDoS (distributed denial-of-service) protection to ensure the site stays operational.
Expert Insight: For most SMB manufacturers, availability is the real priority. They often don’t handle highly sensitive data, so confidentiality is less of a concern. What matters most is uptime: If the production line stops, they lose money immediately. Security controls that create unnecessary downtime are seen as a bigger problem than the security risks themselves.
Secure Your Data
Whether you need to ensure your data remains confidential, free from tampering or available, we’re here to help!
Contact us to schedule a meeting, and let’s create an IT plan that is built around your priorities.
Stay updated! Get tips and insights delivered to your inbox weekly by subscribing to our newsletter.











