Vulnerability Scanning vs. Penetration Testing: What’s the Difference?
As a small business, there is a plethora of cybersecurity tools available to protect your data, network and applications until you’re blue in the face.
But how do you know those tools are working or properly configured?
Managed service providers (MSPs) generally offer vulnerability scanning and penetration testing to help their clients find holes in their network that could be exploited by attackers.
- Vulnerability scanning: A lighter approach using automated tools that scan systems for known vulnerabilities.
- Penetration testing: A heavier approach where a simulated cyberattack is used to exploit vulnerabilities.
Each of these security testing methods can be performed externally or internally.
These approaches differ, not only in their core function, but also in levels of disruption and cost for the client.
Let’s discuss both security testing methods, and how the internal and external versions differ.
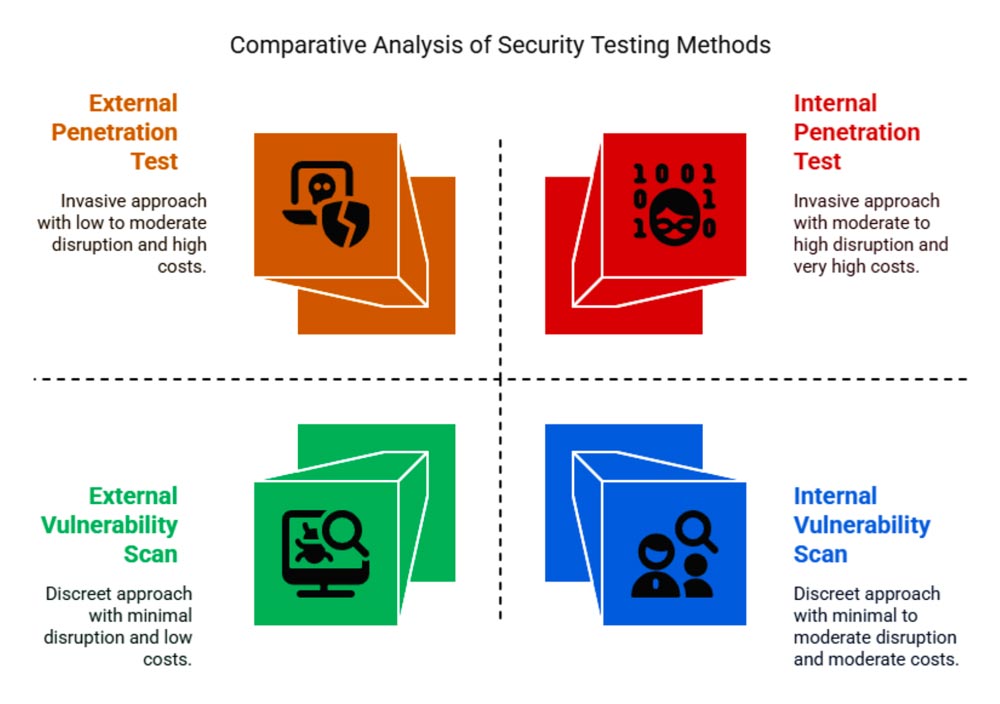
Test Type | Scope | Approach | Disruption | Cost |
Vulnerability Scan | External | Observational discovery of known weaknesses | Low | Low |
Vulnerability Scan | Internal | Observational assessment of internal systems & configurations | Moderate | Moderate |
Penetration Test | External | Invasive, simulates a real-world outside attacker | High | High |
Penetration Test | Internal | Invasive, simulates insider threat or post-breach activity | Very High | Very High |
Vulnerability Scans
A vulnerability scan is like checking the doors and windows of your house for weaknesses. You’re not actively defending against an attack, but you’re trying to fix any misconfigurations (unlocked doors, cracked windows) that could be exploited.
A misconfigured firewall, a user with elevated privileges and unpatched software are things a vulnerability scan will detect.
As noted earlier, vulnerability scans can be performed both externally and internally.
An external vulnerability scan will detect issues that an attacker on the outside could exploit. You’re trying to keep the bad guys out by patching any holes.
An internal scan will detect issues that an attacker who already has access to your network can exploit. If the bad guys happen to get by your defenses, what can they do once they’re inside?
External scans should come first. Attackers are constantly scanning the internet for open doors, so you want to make sure yours are locked.
Once your perimeter is hardened, you can start internal scans to help reduce risk within your network.
Penetration Tests
A penetration test is like hiring someone to try to break into your house. They are actively trying to gain access, and this simulated test will determine what is and isn’t working.
Just like vulnerability scans, penetration tests can be performed both externally and internally.
An external penetration test will simulate an attacker breaking into your network, targeting assets like your website, email server and VPN.
Vulnerability scans and penetration tests could save you thousands in legal and remediation fees should you fall victim to a cyberattack.
An internal test will determine what the attacker can accomplish once they are inside your network. How easily can they escalate privileges, spread malware and steal credentials?
Again, external penetration tests should be done first to ensure your defenses are secure. Then, you can focus on defending against attacks once a bad actor has broken through.
Some compliance standards require annual penetration testing. It’s not just best practice; it may be mandatory in your industry.
Downtime and Costs
Vulnerability Scans
- Downtime: Minimal to moderate
- Cost: Low
- Frequency: Annually
Vulnerability scans will cause minimal to moderate downtime for the client (with internal scans generally causing more downtime than external scans). Since automated tools simply look for holes, it doesn’t require us to disable aspects of your network; they just run in the background while you work as normal.
And because the tools do all the work, the cost generally is minimal or, oftentimes, included in your monthly subscription.
We recommend our clients have at least one external vulnerability scan per year.
Penetration Tests
- Downtime: Moderate to high
- Cost: High
- Frequency: Quarterly or annually
Penetration tests, on the other hand, require much more time, effort and expertise, which means they come with a much higher cost. An IT technician is needed to perform the test by attempting to break into your network, which could mean temporarily disabling parts of your network to simulate attacks.
Many MSPs categorize them as projects billed outside the normal monthly subscription.
External tests come with less downtime than internal tests, so keep that in mind when scheduling.
But because they are much more invasive and simulate real attacks, we work with our clients to pick a time and date that works best for them to minimize downtime.
Catch Vulnerabilities Before Bad Guys Can Exploit Them
Vulnerability scans and penetration tests could save you thousands in legal and remediation fees should you fall victim to a cyberattack.
Contact us to schedule a consultation. We’ll discuss how to implement these security testing methods for your organization so you can focus on running your business.
Stay updated! Get tips and insights delivered to your inbox weekly by subscribing to our newsletter.